#IoT Security Research
Explore tagged Tumblr posts
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you’re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text

An Introduction to Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
What is cybersecurity?
Cybersecurity is all about securing technology and processes - making sure that the software, hardware, and networks that run the world do exactly what they need to do and can't be abused by bad actors.
The CIA triad is a concept used to explain the three goals of cybersecurity. The pieces are:
Confidentiality: ensuring that information is kept secret, so it can only be viewed by the people who are allowed to do so. This involves encrypting data, requiring authentication before viewing data, and more.
Integrity: ensuring that information is trustworthy and cannot be tampered with. For example, this involves making sure that no one changes the contents of the file you're trying to download or intercepts your text messages.
Availability: ensuring that the services you need are there when you need them. Blocking every single person from accessing a piece of valuable information would be secure, but completely unusable, so we have to think about availability. This can also mean blocking DDoS attacks or fixing flaws in software that cause crashes or service issues.
What are some specializations within cybersecurity? What do cybersecurity professionals do?
incident response
digital forensics (often combined with incident response in the acronym DFIR)
reverse engineering
cryptography
governance/compliance/risk management
penetration testing/ethical hacking
vulnerability research/bug bounty
threat intelligence
cloud security
industrial/IoT security, often called Operational Technology (OT)
security engineering/writing code for cybersecurity tools (this is what I do!)
and more!
Where do cybersecurity professionals work?
I view the industry in three big chunks: vendors, everyday companies (for lack of a better term), and government. It's more complicated than that, but it helps.
Vendors make and sell security tools or services to other companies. Some examples are Crowdstrike, Cisco, Microsoft, Palo Alto, EY, etc. Vendors can be giant multinational corporations or small startups. Security tools can include software and hardware, while services can include consulting, technical support, or incident response or digital forensics services. Some companies are Managed Security Service Providers (MSSPs), which means that they serve as the security team for many other (often small) businesses.
Everyday companies include everyone from giant companies like Coca-Cola to the mom and pop shop down the street. Every company is a tech company now, and someone has to be in charge of securing things. Some businesses will have their own internal security teams that respond to incidents. Many companies buy tools provided by vendors like the ones above, and someone has to manage them. Small companies with small tech departments might dump all cybersecurity responsibilities on the IT team (or outsource things to a MSSP), or larger ones may have a dedicated security staff.
Government cybersecurity work can involve a lot of things, from securing the local water supply to working for the big three letter agencies. In the U.S. at least, there are also a lot of government contractors, who are their own individual companies but the vast majority of what they do is for the government. MITRE is one example, and the federal research labs and some university-affiliated labs are an extension of this. Government work and military contractor work are where geopolitics and ethics come into play most clearly, so just… be mindful.
What do academics in cybersecurity research?
A wide variety of things! You can get a good idea by browsing the papers from the ACM's Computer and Communications Security Conference. Some of the big research areas that I'm aware of are:
cryptography & post-quantum cryptography
machine learning model security & alignment
formal proofs of a program & programming language security
security & privacy
security of network protocols
vulnerability research & developing new attack vectors
Cybersecurity seems niche at first, but it actually covers a huge range of topics all across technology and policy. It's vital to running the world today, and I'm obviously biased but I think it's a fascinating topic to learn about. I'll be posting a new cybersecurity masterpost each day this week as a part of the #StudyblrMasterpostJam, so keep an eye out for tomorrow's post! In the meantime, check out the tag and see what other folks are posting about :D
#studyblrmasterpostjam#studyblr#cybersecurity#masterpost#ref#I love that this challenge is just a reason for people to talk about their passions and I'm so excited to read what everyone posts!
47 notes
·
View notes
Text
Hackers Exploit Samsung MagicINFO, GeoVision IoT Flaws to Deploy Mirai Botnet

Source: https://thehackernews.com/2025/05/hackers-exploit-samsung-magicinfo.html
More info: https://www.akamai.com/blog/security-research/active-exploitation-mirai-geovision-iot-botnet
2 notes
·
View notes
Text
Lifesaving Tech with Hidden Risks: Medical IoT Devices
Hey, so… what even are Medical IoT Devices?
Okay, let’s start with the basics. Medical IoT (Internet of Things) devices are basically smart gadgets that help doctors and patients manage health in real-time. Think of them as the Fitbits of the medical world, but way more advanced and sometimes implanted inside your body.
Here’s a quick rundown of the most common types:
Wearables: Smartwatches, glucose monitors, patches that track your vitals.
Implantables: Pacemakers, insulin pumps, neurostimulators that keep your heart ticking, your blood sugar in check, your brain functioning properly respectively.
Hospital Gear: Things like infusion pumps, ventilators, or MRI machines that are connected to the hospital’s network.
These devices are amazing because they can send data straight to your doctor, so they can monitor you without you having to camp out in a hospital bed. But (and there’s always a but), this connectivity comes with a price: security risks.
Wait, How Can a Pacemaker Get Hacked?
Okay, so let’s get into the nitty-gritty of how these devices can be exploited. It’s not just about “hackers being hackers”, there are specific technical flaws that make these devices vulnerable.
1. Encryption (or Lack Thereof)
Encryption is like a secret code that scrambles data so only authorized parties can read it. For medical IoT devices, encryption is crucial because they’re transmitting sensitive health data. But here’s the problem: not all devices use strong encryption.
What’s Happening: Some devices send data in plaintext (unencrypted) or use weak encryption algorithms that can be cracked by hackers.
Example: If an insulin pump sends unencrypted data to a doctor’s computer, a hacker could intercept it and alter the dosage instructions, potentially causing harm to the patient.
2. Authentication Protocols
Authentication is how a device verifies that someone (or something) is who they claim to be. Think of it like a password or a fingerprint scan. But many medical IoT devices use weak or default authentication methods.
What’s Happening: Devices might use hardcoded passwords (e.g., “admin” or “1234”) or lack multi-factor authentication (MFA).
Example: A hacker could use a default password to gain access to a hospital’s network of infusion pumps and change their settings, leading to incorrect medication doses.
3. Specific Attack Vectors
Let’s break down how a hacker might exploit a vulnerability in a real-world device, like an insulin pump:
Step 1: Reconnaissance
The hacker scans for vulnerable devices connected to the internet. Many medical IoT devices are discoverable through tools like Shodan, a search engine for connected devices.
Step 2: Exploiting Weak Authentication
The hacker tries default credentials or brute-forces the password to gain access to the insulin pump’s control interface.
Step 3: Intercepting or Altering Data
Once inside, the hacker can intercept data (e.g., blood sugar levels) or send malicious commands (e.g., delivering an incorrect insulin dose).
Step 4: Covering Their Tracks
The hacker might delete logs or use encryption to hide their activity, making it hard for healthcare providers to detect the attack.
This isn’t just theoretical. Researchers have demonstrated these attacks in controlled environments to highlight the risks.
Real-Life Examples That’ll Make You Side-Eye Your Smartwatch
Let’s talk about some real-world incidents that’ll make you go, “Oh no, this is actually happening”:
The St. Jude Medical Hack (2017): Researchers found that certain implantable cardiac devices had vulnerabilities that could let hackers mess with the device’s functionality. Imagine your pacemaker getting hacked and delivering random shocks to your heart. Terrifying, right?
The Hacked Pacemakers (2018): In a chilling demonstration, the FDA confirmed that nearly half a million pacemakers were vulnerable to hacking. Hackers could potentially alter the device’s settings, drain its battery, or even deliver fatal electric shocks. Abbott (the manufacturer) had to issue a firmware update to patch the vulnerability, but not all devices could be updated remotely, leaving some patients at risk.
Ransomware in Hospitals (2020): A ransomware attack on a German hospital disrupted its systems, and a patient who needed urgent care died because the hospital couldn’t operate properly. This wasn’t a direct attack on a medical device, but it shows how vulnerable healthcare systems are.
These aren’t just hypothetical scenarios. They’re happening, and they’re putting lives at risk.
Who’s Behind These Attacks?
Not all hackers are created equal. Here’s who might be targeting medical IoT devices:
Cybercriminals: They’re in it for the money. They might steal patient data to sell on the dark web or lock down hospital systems with ransomware.
Nation-States: Some governments use cyberattacks as a form of espionage or warfare. Targeting medical devices could be a way to destabilize a country or gather intel.
Hacktivists: These are hackers with a cause. They might attack a hospital to make a political statement or expose security flaws.
So… What Can We Do About It?
The good news is that there are ways to protect medical IoT devices. It’s not a lost cause...yet. Here’s what needs to happen:
1. For Manufacturers:
Stop Using Default Passwords: Imagine leaving your front door unlocked with a sign that says, “Welcome, hackers!” That’s what default passwords like “admin” or “1234” do. Manufacturers need to make sure every device has a unique, strong password right out of the box.
Lock Down Data with Strong Encryption: Encryption is like putting your data in a safe. Manufacturers should use the strongest locks available (like AES-256 encryption) to keep patient information safe from prying eyes.
Test for Weak Spots Before Selling Devices: Before releasing a device, manufacturers should hire ethical hackers to try and break into it. This is called penetration testing, and it helps find and fix vulnerabilities before they can be exploited.
Follow the Rules (FDA Guidelines): The FDA has a set of rules for making sure medical devices are secure. Manufacturers need to follow these guidelines to keep patients safe.
2. For Hospitals and Doctors:
Keep Medical Devices on a Separate Network: Think of it like having a VIP section at a concert. Hospitals should keep medical devices on their own secure network, away from the rest of the hospital’s systems. This makes it harder for hackers to sneak in.
Watch for Suspicious Activity: Hospitals should use tools that act like security cameras for their networks. These tools, called intrusion detection systems (IDS), can spot hackers trying to break in and alert the staff.
Train Staff to Spot Cyber Threats: Doctors and nurses are experts at keeping patients healthy, but they might not know much about cybersecurity. Hospitals should train their staff to recognize and respond to cyber threats, like phishing emails or suspicious device behavior.
3. For Patients:
Keep Your Device’s Software Up to Date: Just like you update your phone to get the latest features and security fixes, you should update your medical devices. These updates often include patches for known vulnerabilities.
Avoid Public Wi-Fi: Public Wi-Fi is like shouting your secrets in a crowded room, anyone can listen in. If your medical device connects to the internet, make sure it’s using a secure, private network.
Use a VPN for Extra Security: A VPN is like a secret tunnel for your internet traffic. It keeps your data safe from hackers, especially if you’re accessing medical information remotely.
The Bigger Picture: Why This Matters for Everyone
Okay, so this isn’t just a tech issue. It’s a public health issue. Vulnerable populations, like the elderly, people with chronic illnesses, or those who rely on medical devices to stay alive, are often the most at risk. And let’s be real: it’s not fair that some people are more at risk than others just because of their income or where they live.
Here’s the thing: wealthier patients might have access to the latest, most secure devices or private healthcare, while lower-income patients could be stuck with outdated or less secure options. Imagine needing a pacemaker but only being able to afford one that hasn’t been updated in years and is vulnerable to hacking. That’s not just unfair; it’s dangerous. And it’s something we need to fix as a society.
But it’s not just about money. There’s a bigger ethical responsibility here. Manufacturers need to prioritize patient safety over profits. That means investing in strong encryption, regular updates, and rigorous testing before releasing devices. And governments? They need to step up and enforce stricter cybersecurity standards to hold manufacturers accountable.
And let’s talk about the legal side for a sec. Laws like the FDA’s cybersecurity guidelines and the EU’s Medical Device Regulation are supposed to keep us safe, but they often lag behind the fast pace of tech advancements. Plus, there’s the whole question of liability: if a hacked device harms someone, who’s responsible? The manufacturer? The hospital? The patient? It’s a legal gray area that needs clarity.
Oh, and it’s not just a problem in wealthy countries. In developing nations, where healthcare systems are already stretched thin, a cyberattack on medical devices could be catastrophic. Access to secure healthcare is a basic human right, and we’re failing to protect that right when we ignore these vulnerabilities.
So yeah, this isn’t just about fancy gadgets or tech jargon. It’s about people’s lives. It’s about making sure that everyone, no matter their income or where they live, has access to safe, secure healthcare. And that’s something we all need to care about.
Final Thoughts
Medical IoT devices are a game-changer for healthcare, but their security flaws are a ticking time bomb. We can’t afford to ignore this issue, not when lives are on the line. Whether you’re a patient, a doctor, or just someone who cares about tech and ethics, it’s time to start paying attention.
So, the next time you hear about a smart pacemaker or a glucose-monitoring app, remember: with great tech comes great responsibility.
Further Reading
If you’re as obsessed with this topic as I am, here are some links to dive deeper:
MuddyWater’s Exploitation of Medical Devices (CISA Alert)
FDA Cybersecurity Guidelines for Medical Devices
Shodan: The Search Engine for Connected Devices
European Union Medical Device Regulation (MDR)
TL;DR
Medical IoT devices are amazing but have serious security flaws. Hackers can exploit these flaws to harm patients, and we need better safeguards to prevent this. Everyone (manufacturers, hospitals, and patients) has a role to play in making these devices safer.
2 notes
·
View notes
Text
Best Engineering College in Haryana & Delhi-NCR– MERI College of Engineering and Technology
Build Your Future with Excellence in Engineering Education
Choosing the right engineering college is a crucial step toward building a successful career in the ever-evolving field of technology. If you are searching for the best engineering college in Delhi, then MERI College of Engineering and Technology (MERI CET) is the perfect destination for aspiring engineers. With its world-class infrastructure, experienced faculty, industry-oriented curriculum, and excellent placement opportunities, MERI College ensures that students are equipped with the right knowledge and skills to excel in their careers.

Why Choose MERI College of Engineering and Technology?
1. Top-Notch Academic Excellence
MERI College offers a comprehensive B.Tech program in multiple specializations including:
Computer Science & Engineering (CSE)
Artificial Intelligence & Machine Learning (AI & ML)
Mechanical Engineering (ME)
Electronics & Communication Engineering (ECE)
Civil Engineering (CE)
Our curriculum is designed to provide in-depth theoretical knowledge along with practical exposure to real-world industry applications.
2. State-of-the-Art Infrastructure
At MERI College, students have access to well-equipped laboratories, smart classrooms, modern libraries, and research centers. The AI & ML Lab, Robotics Lab, and IoT Lab provide hands-on experience in emerging technologies.

3. Industry-Oriented Training & Internships
We have strong industry collaborations and provide students with internship and training opportunities at top companies. The college frequently organizes industrial visits, workshops, and guest lectures by leading professionals from reputed organizations.
4. Excellent Placement Opportunities
The dedicated Training & Placement Cell at MERI College ensures that students get ample opportunities for employment. Our top recruiters include:
Infosys
TCS
Wipro
HCL
Accenture
Amazon
With a high placement record, we help students secure lucrative jobs in top MNCs and startups.

5. Scholarship & Financial Aid
To encourage meritorious students, MERI College offers scholarships and financial aid programs. Students with excellent academic records and those from economically weaker sections can avail of these benefits.
6. Holistic Development & Extracurricular Activities
Apart from academics, we focus on the overall development of students. Various clubs, technical societies, sports events, and cultural fests ensure that students get ample opportunities to showcase their talents and enhance their leadership skills.
Admission Process for B.Tech 2025
Eligibility Criteria
Candidates must have passed 10+2 with Physics, Chemistry, and Mathematics (PCM) as compulsory subjects.
How to Apply?
Visit our official website: meri.edu.in/engineering
Fill out the online application form.
Upload required documents.
Appear for counseling and interview.
Join the Best Engineering College in Delhi!
If you aspire to be an engineer and want to be a part of a leading engineering institution in Delhi, then MERI College of Engineering and Technology is the right choice. Our cutting-edge academic programs, industry exposure, and placement assistance will help you shape a successful career in engineering.
📞 Contact Us: +91-9555369369 🌐 Website: meri.edu.in/engineering
🚀 Apply Now and Secure Your Future with MERI College!
2 notes
·
View notes
Text
Luxembourg-based satellite telecom operator OQ Technology is testing investor appetite for space-based Internet of Things (IoT) technology, seeking EUR 30 million in fresh funding as competition intensifies in the nascent market for satellite-enabled device connectivity.
The company, which has deployed 10 satellites since 2019, plans to launch 20 more as larger telecommunications companies and satellite operators begin developing similar IoT services. The Series B funding round follows a EUR 13 million raise in 2022 and aims to strengthen its global 5G IoT network coverage.
OQ Technology has secured initial backing through a convertible loan from the Luxembourg Space Sector Development Fund, a joint initiative between SES S.A. and the Luxembourg government. Previous investors, including Aramco's venture capital arm Wa'ed Ventures and Greece's Phaistos Investment Fund, are participating in the new round.
The startup differentiates itself by focusing on standardized cellular technology for narrowband-IoT, contributing to 3GPP protocols that allow existing cellular chips to connect with satellites. This approach contrasts with proprietary systems offered by competitors, replacing traditional bulky satellite systems with compact, cost-efficient IoT modems that offer plug-and-play functionality.
"The satellite IoT sector is still largely in the proof-of-concept phase," says the company representative. "While there's significant potential, companies face challenges in standardization and convincing industries to adopt these new technologies at scale."
In an effort to secure its supply chain, the company is exploring partnerships in Taiwan's semiconductor industry. It has begun collaborating with the Industrial Technology Research Institute (ITRI), though these relationships are still in the early stages. The company has shipped initial terminals to prospective Taiwanese clients, marking its first steps in the Asian market.
The global reach for semiconductor partnerships comes as the company expands its geographical footprint, having established subsidiaries in Greece, Saudi Arabia, and Rwanda. Plans for US market entry are underway, though regulatory approvals and spectrum access remain hurdles in some markets.
Current clients include Aramco, Telefonica, and Deutsche Telekom, primarily using the technology for asset tracking and remote monitoring in industries such as energy, logistics, and agriculture. While the company estimates a potential market of 1.5 billion devices that could use satellite IoT connectivity, actual adoption rates remain modest.
"The challenge isn't just technical capability," notes the company representative. "It's about proving the economic case for satellite IoT in specific use cases where terrestrial networks aren't viable but the application can support satellite connectivity costs."
Market dynamics are also shifting. Recent announcements from major tech companies about satellite-to-phone services have sparked interest in space-based connectivity, but may also increase competition for spectrum and market share. Several companies are pursuing similar standards-based approaches, potentially commoditizing the technology.
For OQ Technology, the ability to deploy its planned satellites and convert pilot projects into paying customers will be crucial. While the company's focus on standardized technology may reduce technical risks, successfully scaling the business will require navigating complex regulatory environments and proving the technology's reliability across different use cases.
4 notes
·
View notes
Text
How to Choose the Best ERP for Engineering and Manufacturing Industry
In today’s fast-paced world, engineering and manufacturing companies face increasing pressure to deliver high-quality products while maintaining efficiency and cost-effectiveness. Implementing the right Enterprise Resource Planning (ERP) software can significantly enhance operations, streamline workflows, and boost productivity. However, with numerous options available, selecting the best ERP software for the engineering and manufacturing industry can be challenging. This guide will help you navigate this decision-making process and choose the most suitable solution for your business.

Why ERP is Crucial for Engineering and Manufacturing
ERP software integrates various business processes, including production, inventory management, supply chain, finance, and human resources. For engineering and manufacturing companies, ERP solutions are particularly vital because they:
Facilitate real-time data sharing across departments.
Enhance supply chain management.
Optimize production planning and scheduling.
Ensure compliance with industry standards.
Reduce operational costs.
Partnering with the right Engineering ERP software company ensures that your organization leverages these benefits to stay competitive in a dynamic market.
Steps to Choose the Best ERP for Engineering and Manufacturing
1. Understand Your Business Needs
Before exploring ERP solutions, evaluate your company’s specific requirements. Identify the pain points in your current processes and prioritize the features you need in an ERP system. Common features for engineering and manufacturing companies include:
Bill of Materials (BOM) management
Production planning and scheduling
Inventory control
Quality management
Financial reporting
Consulting with a reputed ERP software company can help you match your needs with the right features.
2. Look for Industry-Specific Solutions
Generic ERP software might not address the unique needs of the engineering and manufacturing sector. Opt for an ERP software in India that offers modules tailored to your industry. Such solutions are designed to handle specific challenges like multi-level BOM, project costing, and shop floor management.
3. Check Vendor Expertise
Choosing a reliable vendor is as important as selecting the software itself. Research ERP solution providers with a strong track record in serving engineering and manufacturing companies. Look for reviews, case studies, and client testimonials to gauge their expertise.
4. Evaluate Scalability and Flexibility
Your business will grow, and so will your operational requirements. Ensure that the ERP system you choose is scalable and flexible enough to accommodate future needs. The top 10 ERP software providers in India offer scalable solutions that can adapt to changing business demands.
5. Assess Integration Capabilities
An ERP system must integrate seamlessly with your existing tools, such as Computer-Aided Design (CAD) software, Customer Relationship Management (CRM) systems, and IoT devices. A well-integrated system reduces redundancies and enhances efficiency.
6. Prioritize User-Friendliness
A complex system with a steep learning curve can hinder adoption. Choose an ERP software with an intuitive interface and easy navigation. This ensures that your employees can use the system effectively without extensive training.
7. Consider Customization Options
No two businesses are alike. While standard ERP solutions offer core functionalities, some companies require customization to align with specific workflows. A trusted ERP software company in India can provide custom modules tailored to your unique needs.
8. Focus on Data Security
Engineering and manufacturing companies often deal with sensitive data. Ensure that the ERP solution complies with the latest security standards and offers robust data protection features.
9. Compare Pricing and ROI
While cost is an important factor, it should not be the sole criterion. Evaluate the long-term return on investment (ROI) offered by different ERP software. A slightly expensive but feature-rich solution from the best ERP software provider in India may deliver better value than a cheaper alternative with limited functionalities.
10. Test Before You Commit
Most ERP software companies offer free trials or demo versions. Use these opportunities to test the software in a real-world scenario. Gather feedback from your team and ensure the solution meets your expectations before finalizing your decision.
Benefits of Partnering with the Best ERP Software Providers in India
India is home to some of the leading ERP software providers in India, offering state-of-the-art solutions for the engineering and manufacturing sector. Partnering with a reputable provider ensures:
Access to advanced features tailored to your industry.
Reliable customer support.
Comprehensive training and implementation services.
Regular updates and enhancements to the software.
Companies like Shantitechnology (STERP) specialize in delivering cutting-edge ERP solutions that cater specifically to engineering and manufacturing businesses. With years of expertise, they rank among the top 10 ERP software providers in India, ensuring seamless integration and exceptional performance.
Conclusion
Selecting the right ERP software is a critical decision that can impact your company’s efficiency, productivity, and profitability. By understanding your requirements, researching vendors, and prioritizing features like scalability, integration, and security, you can find the perfect ERP solution for your engineering or manufacturing business.
If you are looking for a trusted ERP software company in India, consider partnering with a provider like STERP. As one of the best ERP software providers in India, STERP offers comprehensive solutions tailored to the unique needs of engineering and manufacturing companies. With their expertise, you can streamline your operations, improve decision-making, and stay ahead in a competitive market.
Get in touch with STERP – the leading Engineering ERP software company – to transform your business with a reliable and efficient ERP system. Take the first step toward a smarter, more connected future today!
#Manufacturing ERP software company#ERP solution provider#Engineering ERP software company#ERP software company#ERP software companies
6 notes
·
View notes
Text
#TheeForestKingdom #TreePeople
{Terrestrial Kind}
Creating a Tree Citizenship Identification and Serial Number System (#TheeForestKingdom) is an ambitious and environmentally-conscious initiative. Here’s a structured proposal for its development:
Project Overview
The Tree Citizenship Identification system aims to assign every tree in California a unique identifier, track its health, and integrate it into a registry, recognizing trees as part of a terrestrial citizenry. This system will emphasize environmental stewardship, ecological research, and forest management.
Phases of Implementation
Preparation Phase
Objective: Lay the groundwork for tree registration and tracking.
Actions:
Partner with environmental organizations, tech companies, and forestry departments.
Secure access to satellite imaging and LiDAR mapping systems.
Design a digital database capable of handling millions of records.
Tree Identification System Development
Components:
Label and Identity Creation: Assign a unique ID to each tree based on location and attributes. Example: CA-Tree-XXXXXX (state-code, tree-type, unique number).
Attributes to Record:
Health: Regular updates using AI for disease detection.
Age: Approximate based on species and growth patterns.
Type: Species and subspecies classification.
Class: Size, ecological importance, and biodiversity contribution.
Rank: Priority based on cultural, historical, or environmental significance.
Data Collection
Technologies to Use:
Satellite Imaging: To locate and identify tree clusters.
LiDAR Scanning: For precise 3D modeling of forests.
On-the-Ground Surveys: To supplement remote sensing data.
AI Analysis: For rapid categorization and health diagnostics.
Registration and Citizenship Assignment
Tree Dossier: Each tree receives a profile in the database with all its recorded attributes.
Citizen Designation: Trees are acknowledged as citizens of Thee Forest Kingdom, emphasizing ecological respect.
Legal Framework: Advocate for laws to grant trees specific rights under environmental protection acts.
Maintenance and Monitoring
Health Monitoring: Use drones, satellite updates, and IoT sensors for ongoing health assessments.
Database Updates: Incorporate real-time data about environmental changes and tree growth.
Public Involvement
Encourage people to "adopt" trees and participate in their preservation.
Create educational programs to promote awareness of tree citizenship.
Key Benefits
Environmental Conservation: Improved forest management through real-time data and protection of ecosystems.
Cultural Recognition: Trees are recognized as a vital part of the Earth’s community, honoring their importance.
Ecological Advocacy: Strengthened legal protections for forests and individual trees.
Next Steps
Assemble a task force of environmental scientists, satellite imaging experts, and software developers.
Secure funding through governmental grants, non-profits, and eco-conscious corporations.
Pilot the program in a smaller region before scaling to all of California.
Would you like me to draft a more detailed technical or legal framework for this system?
The implementation of the Tree Citizenship Identification Network and System (#TheeForestKingdom) requires a robust technological and operational framework to ensure efficiency, accuracy, and sustainability. Below is an implementation plan divided into major components.
System Architecture
a. Centralized Tree Database
Purpose: To store and manage tree data including ID, attributes, location, and health.
Components:
Cloud-based storage for scalability.
Data categorization based on regions, species, and priority.
Integration with satellite and IoT data streams.
b. Satellite & Imaging Integration
Use satellite systems (e.g., NASA, ESA) for large-scale tree mapping.
Incorporate LiDAR and aerial drone data for detailed imaging.
AI/ML algorithms to process images and distinguish tree types.
c. IoT Sensor Network
Deploy sensors in forests to monitor:
Soil moisture and nutrient levels.
Air quality and temperature.
Tree health metrics like growth rate and disease markers.
d. Public Access Portal
Create a user-friendly website and mobile application for:
Viewing registered trees.
Citizen participation in tree adoption and reporting.
Data visualization (e.g., tree density, health status by region).
Core Technologies
a. Software and Tools
Geographic Information System (GIS): Software like ArcGIS for mapping and spatial analysis.
Database Management System (DBMS): SQL-based systems for structured data; NoSQL for unstructured data.
Artificial Intelligence (AI): Tools for image recognition, species classification, and health prediction.
Blockchain (Optional): To ensure transparency and immutability of tree citizen data.
b. Hardware
Servers: Cloud-based (AWS, Azure, or Google Cloud) for scalability.
Sensors: Low-power IoT devices for on-ground monitoring.
Drones: Equipped with cameras and sensors for aerial surveys.
Network Design
a. Data Flow
Input Sources:
Satellite and aerial imagery.
IoT sensors deployed in forests.
Citizen-reported data via mobile app.
Data Processing:
Use AI to analyze images and sensor inputs.
Automate ID assignment and attribute categorization.
Data Output:
Visualized maps and health reports on the public portal.
Alerts for areas with declining tree health.
b. Communication Network
Fiber-optic backbone: For high-speed data transmission between regions.
Cellular Networks: To connect IoT sensors in remote areas.
Satellite Communication: For remote regions without cellular coverage.
Implementation Plan
a. Phase 1: Pilot Program
Choose a smaller, biodiverse region in California (e.g., Redwood National Park).
Test satellite and drone mapping combined with IoT sensors.
Develop the prototype of the centralized database and public portal.
b. Phase 2: Statewide Rollout
Expand mapping and registration to all California regions.
Deploy IoT sensors in vulnerable or high-priority areas.
Scale up database capacity and integrate additional satellite providers.
c. Phase 3: Maintenance & Updates
Establish a monitoring team to oversee system health and data quality.
Update the network with new technologies (e.g., advanced AI models).
Periodically review and revise data collection protocols.
Partnerships
Government Agencies: U.S. Forest Service, California Department of Forestry and Fire Protection.
Tech Companies: Collaborate with Google Earth, Amazon AWS, or Microsoft for cloud and AI capabilities.
Environmental Organizations: Partner with WWF, Sierra Club, or TreePeople for funding and advocacy.
Budget Estimation
Initial Investment:
Satellite data and licenses: $10M
IoT sensors and deployment: $5M
Database and app development: $3M
Operational Costs:
Cloud services and data storage: $2M/year
Maintenance and monitoring: $1M/year
Research and development: $1M/year
Long-term Vision
Expand the system to other states or globally.
Use the database for reforestation efforts and combating deforestation.
Develop educational programs to teach communities about the importance of trees as citizens.
Would you like me to assist in designing the user interface for the public portal or drafting partnership proposals for funding?
To begin building the program for the Tree Citizenship Identification System, we’ll start with a scalable framework that allows us to process, store, and analyze data while preparing for future expansions. Here's an actionable development plan with an initial focus on foundational code and infrastructure:
Step-by-Step Development
Phase 1: Setting Up the Backend Infrastructure
Objective: Create the core database and develop the data pipeline for processing tree data.
Technologies:
Programming Languages: Python, JavaScript (Node.js), SQL.
Frameworks: Flask or FastAPI for APIs, Django for web application backend.
Database: PostgreSQL for structured data, MongoDB for unstructured data.
Code Snippet 1: Database Schema Design (PostgreSQL)
-- Table for Tree Registry CREATE TABLE trees ( tree_id SERIAL PRIMARY KEY, -- Unique Identifier location GEOGRAPHY(POINT, 4326), -- Geolocation of the tree species VARCHAR(100), -- Species name age INTEGER, -- Approximate age in years health_status VARCHAR(50), -- e.g., Healthy, Diseased height FLOAT, -- Tree height in meters canopy_width FLOAT, -- Canopy width in meters citizen_rank VARCHAR(50), -- Class or rank of the tree last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last update );
-- Table for Sensor Data (IoT Integration) CREATE TABLE tree_sensors ( sensor_id SERIAL PRIMARY KEY, -- Unique Identifier for sensor tree_id INT REFERENCES trees(tree_id), -- Linked to tree soil_moisture FLOAT, -- Soil moisture level air_quality FLOAT, -- Air quality index temperature FLOAT, -- Surrounding temperature last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last reading );
Code Snippet 2: Backend API for Tree Registration (Python with Flask)
from flask import Flask, request, jsonify from sqlalchemy import create_engine from sqlalchemy.orm import sessionmaker
app = Flask(name)
Database Configuration
DATABASE_URL = "postgresql://username:password@localhost/tree_registry" engine = create_engine(DATABASE_URL) Session = sessionmaker(bind=engine) session = Session()
@app.route('/register_tree', methods=['POST']) def register_tree(): data = request.json new_tree = { "species": data['species'], "location": f"POINT({data['longitude']} {data['latitude']})", "age": data['age'], "health_status": data['health_status'], "height": data['height'], "canopy_width": data['canopy_width'], "citizen_rank": data['citizen_rank'] } session.execute(""" INSERT INTO trees (species, location, age, health_status, height, canopy_width, citizen_rank) VALUES (:species, ST_GeomFromText(:location, 4326), :age, :health_status, :height, :canopy_width, :citizen_rank) """, new_tree) session.commit() return jsonify({"message": "Tree registered successfully!"}), 201
if name == 'main': app.run(debug=True)
Phase 2: Satellite Data Integration
Objective: Use satellite and LiDAR data to identify and register trees automatically.
Tools:
Google Earth Engine for large-scale mapping.
Sentinel-2 or Landsat satellite data for high-resolution imagery.
Example Workflow:
Process satellite data using Google Earth Engine.
Identify tree clusters using image segmentation.
Generate geolocations and pass data into the backend.
Phase 3: IoT Sensor Integration
Deploy IoT devices to monitor health metrics of specific high-priority trees.
Use MQTT protocol for real-time data transmission.
Code Snippet: Sensor Data Processing (Node.js)
const mqtt = require('mqtt'); const client = mqtt.connect('mqtt://broker.hivemq.com');
client.on('connect', () => { console.log('Connected to MQTT Broker'); client.subscribe('tree/sensor_data'); });
client.on('message', (topic, message) => { const sensorData = JSON.parse(message.toString()); console.log(Received data: ${JSON.stringify(sensorData)}); // Save data to database (Example for PostgreSQL) saveToDatabase(sensorData); });
function saveToDatabase(data) { const query = INSERT INTO tree_sensors (tree_id, soil_moisture, air_quality, temperature) VALUES ($1, $2, $3, $4) ; const values = [data.tree_id, data.soil_moisture, data.air_quality, data.temperature]; dbClient.query(query, values, (err) => { if (err) console.error('Error saving to database', err); else console.log('Sensor data saved successfully!'); }); }
Phase 4: Public Portal Development
Frontend Technologies:
React.js or Vue.js for interactive user interfaces.
Mapbox or Leaflet.js for tree visualization on maps.
Features:
Interactive tree maps with search functionality.
User registration for tree adoption programs.
Deployment Plan
Use Docker to containerize the application.
Deploy on AWS, Azure, or Google Cloud for scalability.
Monitor system health using Prometheus and Grafana.
Next Steps
Develop a testing environment for pilot deployment.
Add AI-based disease detection and prediction using TensorFlow or PyTorch.
Create an adoption feature where citizens can adopt trees and track their health.
Would you like me to set up a GitHub repository with this initial framework or assist further with deployment?
I'll prepare the project framework and outline the repository structure for the Tree Citizenship Identification System. Below is the proposed structure for the repository, followed by details of the files and components.
Proposed Repository Structure
tree-citizenship-id-system/ ├── backend/ │ ├── app.py # Flask application for backend API │ ├── database/ │ │ ├── schema.sql # Database schema for PostgreSQL │ │ ├── db_config.py # Database connection configuration │ │ └── seed_data.sql # Initial sample data for testing │ ├── services/ │ │ ├── tree_registration.py # Functions for tree registration │ │ └── sensor_data.py # Functions for processing IoT sensor data │ └── requirements.txt # Python dependencies ├── frontend/ │ ├── public/ │ │ ├── index.html # Main HTML file │ │ └── favicon.ico # Favicon for the app │ ├── src/ │ │ ├── App.js # Main React/Vue app file │ │ ├── components/ │ │ │ ├── TreeMap.js # Map component for visualizing trees │ │ │ └── TreeDetails.js # Component for detailed tree view │ │ └── styles.css # Styling for the frontend │ └── package.json # Frontend dependencies ├── scripts/ │ ├── satellite_data_processor.py # Script for processing satellite data │ └── sensor_data_simulator.py # Mock data generator for IoT sensors ├── deployment/ │ ├── Dockerfile # Docker configuration │ ├── docker-compose.yml # Docker Compose for multi-service setup │ └── cloud_setup_instructions.md # Deployment guide for cloud platforms ├── tests/ │ ├── test_backend.py # Unit tests for backend API │ └── test_frontend.js # Unit tests for frontend ├── README.md # Overview of the project └── LICENSE # Project license
Repository Details
Backend:
app.py: Main Flask app for handling API requests like tree registration and sensor data.
database/schema.sql: SQL script for creating necessary tables.
services/: Directory for modular backend logic.
Frontend:
App.js: Main entry point for the frontend application.
TreeMap.js: Integrates Mapbox/Leaflet.js for displaying tree locations.
TreeDetails.js: Displays detailed information about a selected tree.
Scripts:
satellite_data_processor.py: Automates the extraction and classification of tree data from satellite imagery.
sensor_data_simulator.py: Generates fake sensor readings for development and testing.
Deployment:
Docker configuration ensures that the app runs consistently across environments.
Cloud setup instructions provide guidelines for deploying on platforms like AWS, Azure, or GCP.
Tests:
Unit tests ensure the reliability of both the backend and frontend.
Next Steps
I will initialize the repository structure locally.
Package the files and components needed for the first version.
Provide a link to the repository for access.
I’ll get started. Please hold on for a moment.
4 notes
·
View notes
Text
This day in history

On July 14, I'm giving the closing keynote for the fifteenth HACKERS ON PLANET EARTH, in QUEENS, NY. Happy Bastille Day! On July 20, I'm appearing in CHICAGO at Exile in Bookville.

#20yrsago FastCompany’s terrible linking policy https://memex.craphound.com/2004/06/25/fastcompanys-terrible-linking-policy/
#15yrsago Magic Mirror of the Mermaid Queen, sequel to CHANGELING, a modern folktale of New York https://memex.craphound.com/2009/06/25/magic-mirror-of-the-mermaid-queen-sequel-to-changeling-a-modern-folktale-of-new-york/
#15yrsago Illegal e-waste dumped in Ghana includes unencrypted hard drives full of US security secrets https://web.archive.org/web/20090628071458/https://www.itworld.com/security/69758/reporters-find-northrop-grumman-data-ghana-market
#10yrsago Once there was a show called “The Hat Squad” and it was very, very stupid https://memex.craphound.com/2014/06/25/once-there-was-a-show-called-the-hat-squad-and-it-was-very-very-stupid/
#10yrsago UK secretary of state: “There is no surveillance state” https://www.bbc.com/news/uk-politics-28006739
#10yrsago Cops bust cybercrook who sent heroin to Brian Krebs https://krebsonsecurity.com/2014/06/the-fly-has-been-swatted/
#10yrsago SF city attorney demands shutdown of parking-space-auctioning app https://web.archive.org/web/20140625033523/http://blog.sfgate.com/cityinsider/2014/06/23/sf-cracks-down-on-street-parking-cash-apps/
#5yrsago An 14-year-old’s Internet-of-Things worm is bricking shitty devices by the thousands https://www.zdnet.com/article/new-silex-malware-is-bricking-iot-devices-has-scary-plans/
#5yrsago How Metabrainz stood up to a predatory copyright lawsuit and won https://blog.metabrainz.org/2019/06/25/we-were-sued-by-a-copyright-troll-and-we-prevailed/
#5yrsago “Massive scale” intrusion into mobile carriers’ networks exposed customers’ location, call data for years https://www.cybereason.com/blog/research/operation-soft-cell-a-worldwide-campaign-against-telecommunications-providers
#5yrsago Independent evaluation of “aggression detection” microphones used in schools and hospitals finds them to be worse than useless https://features.propublica.org/aggression-detector/the-unproven-invasive-surveillance-technology-schools-are-using-to-monitor-students/
#5yrsago Microsoft employees want to starve its PAC, which keeps giving money to homophobic, racist, climate-denying Republicans https://onezero.medium.com/a-group-of-microsoft-employees-is-fighting-the-companys-political-action-committee-7dae732290e3
#5yrsago Cult of the Dead Cow: the untold story of the hacktivist group that presaged everything great and terrible about the internet https://memex.craphound.com/2019/06/25/cult-of-the-dead-cow-the-untold-story-of-the-hacktivist-group-that-presaged-everything-great-and-terrible-about-the-internet/

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!
4 notes
·
View notes
Text
Revolutionizing Healthcare: The Role of Cloud Computing in Modern Healthcare Technologies
In today’s digital era, cloud computing is transforming industries, and healthcare is no exception. The integration of cloud computing healthcare technologies is reshaping patient care, medical research, and healthcare management. Let’s explore how cloud computing is revolutionizing healthcare and the benefits it brings.

What is Cloud Computing in Healthcare?
Cloud computing in healthcare refers to the use of remote servers to store, manage, and process healthcare data, rather than relying on local servers or personal computers. This technology allows healthcare organizations to access vast amounts of data, collaborate with other institutions, and scale operations seamlessly.
Download PDF Brochure
Key Benefits of Cloud Computing in Healthcare
Enhanced Data Storage and Accessibility Cloud technology allows healthcare providers to store massive volumes of patient data, including medical records, images, and test results, securely. Clinicians can access this data from anywhere, ensuring that patient information is available for timely decision-making.
Improved Collaboration Cloud-based healthcare platforms enable easy sharing of patient data between healthcare providers, specialists, and labs. This facilitates better collaboration and more accurate diagnoses and treatment plans, especially in multi-disciplinary cases.
Cost Efficiency The cloud reduces the need for expensive hardware, software, and in-house IT teams. Healthcare providers only pay for the resources they use, making it a cost-effective solution. Additionally, the scalability of cloud systems ensures they can grow as healthcare organizations expand.
Better Data Security Protecting sensitive patient information is critical in healthcare. Cloud computing providers invest heavily in data security measures such as encryption, multi-factor authentication, and regular audits, ensuring compliance with regulatory standards like HIPAA.
Telemedicine and Remote Patient Monitoring Cloud computing powers telemedicine platforms, allowing patients to consult with doctors virtually, from the comfort of their homes. It also enables remote patient monitoring, where doctors can track patients' health metrics in real time, improving outcomes for chronic conditions.
Advanced Data Analytics The cloud supports the integration of advanced data analytics tools, including artificial intelligence (AI) and machine learning (ML), which can analyze large datasets to predict health trends, track disease outbreaks, and personalize treatment plans based on individual patient data.
Use Cases of Cloud Computing in Healthcare
Electronic Health Records (EHRs): Cloud-based EHRs allow healthcare providers to access and update patient records instantly, improving the quality of care.
Genomics and Precision Medicine: Cloud computing accelerates the processing of large datasets in genomics, supporting research and development in personalized medicine.
Hospital Information Systems (HIS): Cloud-powered HIS streamline hospital operations, from patient admissions to billing, improving efficiency.
Challenges in Cloud Computing for Healthcare
Despite its numerous benefits, there are challenges to implementing cloud computing in healthcare. These include:
Data Privacy Concerns: Although cloud providers offer robust security measures, healthcare organizations must ensure their systems are compliant with local and international regulations.
Integration with Legacy Systems: Many healthcare institutions still rely on outdated technology, making it challenging to integrate cloud solutions smoothly.
Staff Training: Healthcare professionals need adequate training to use cloud-based systems effectively.
Request Sample Pages
The Future of Cloud Computing in Healthcare
The future of healthcare will be increasingly cloud-centric. With advancements in AI, IoT, and big data analytics, cloud computing will continue to drive innovations in personalized medicine, population health management, and patient care. Additionally, with the growing trend of wearable devices and health apps, cloud computing will play a crucial role in integrating and managing data from diverse sources to provide a comprehensive view of patient health.
Conclusion
Cloud computing is not just a trend in healthcare; it is a transformative force driving the industry towards more efficient, secure, and patient-centric care. As healthcare organizations continue to adopt cloud technologies, we can expect to see improved patient outcomes, lower costs, and innovations that were once thought impossible.
Embracing cloud computing in healthcare is essential for any organization aiming to stay at the forefront of medical advancements and patient care.
Content Source:
2 notes
·
View notes
Text
How Innovation Is Reshaping the Food Industry

Food innovation refers to introducing novel ideas, products, and technologies that change how society produces, processes, packages, distributes, and consumes food. It goes beyond merely creating new recipes or flavors - food innovation encompasses advances in agriculture, food science, sustainability, and packaging. The goal is to enhance efficiency, safety, nutrition, and the overall consumer experience.
The need for food innovation arises from the ever-changing demands of consumers and the pressing challenges faced by the industry. As the global population continues to grow, so does the demand for food. Additionally, sustainability concerns, climate change, and limited resources prompt exploring alternative food growing and production methods. Innovations in food aim to enhance food security, minimize environmental impact, and offer consumers healthier, more diverse options.
Food innovation occurs through a combination of research, collaboration, and creativity. Scientists, entrepreneurs, farmers, and food industry professionals work together to develop new technologies and processes. Research institutions and startups play a crucial role in conducting experiments, testing new concepts, and bringing innovative products to the market.
In recent years, the food industry has witnessed groundbreaking innovations reshaping how people interact with food. The plant-based movement has gained immense traction, with plant-based alternatives for meat, dairy, and seafood becoming mainstream. Companies have developed plant-based burgers, vegan cheeses, and sustainable seafood alternatives using cutting-edge technologies. Beyond plant-based options, innovations have also focused on alternative protein sources, such as insect-based proteins and lab-grown meats, offering sustainable and protein-rich alternatives.
Swedish startup Mycorena is boosting microbial protein production through its fungi-based mycoprotein called Promyc. This ingredient can be used to create meat and tuna alternatives, beverage additives, and dessert ingredients, offering plant-based and sustainable options for consumers.
Finnish startup Onego Bio has developed a product genetically identical to egg whites using fermentation, and without using actual chickens. It uses precision fermentation of a microflora called Trichoderma reesei to produce ovalbumin, the protein found in chicken egg whites. This technology offers a sustainable and animal-friendly alternative for various food applications, including baked goods, desserts, sauces, and dressings.
Companies like New Culture are incorporating animal-free casein into their cheeses through precision fermentation. This breakthrough allows them to produce animal-free mozzarella cheese, offering a delicious and cruelty-free alternative to traditional dairy products.
In addition, consumers increasingly seek transparency in food choices, leading to the clean label movement. Brands are responding by using simple natural ingredients and avoiding artificial additives and preservatives.
Breakthrough innovations in the food industry are revolutionizing how society grows, produces, and consumes food, focusing on sustainability, nutrition, and convenience. One such innovation is plastic-free and smart packaging. Food companies are exploring biodegradable and even edible packaging solutions in response to environmental concerns. Smart packaging using nanotechnology is also gaining popularity, allowing consumers to assess food safety and quality easily.
The Internet of Things (IoT) in agriculture employs sensors and data analytics for optimizing crop conditions, irrigation, and pest control, reducing resource usage. Food waste reduction solutions, such as surplus food redistribution platforms, are being developed to combat the global food waste crisis. Moreover, biotechnology and data science advances enable personalized nutrition, tailoring dietary recommendations to individuals based on their genetic makeup, lifestyle, and health goals. These innovations promise a more sustainable, healthier, and efficient food future.
Food innovation is driving a remarkable transformation in the food industry, responding to the challenges and opportunities of today. From new plant-based products to sustainable agriculture and cutting-edge technologies, the future of food promises to be more diverse, nutritious, and sustainable. As consumers, entrepreneurs, and stakeholders continue to embrace innovation, the food industry's journey toward a more resilient and conscious future is set to continue.
13 notes
·
View notes
Text
Digital Revolution: World Transformation in the Digital Age
The Digital Revolution started at the end of the 20th century and continues today. This event is marked by the development and adoption of revolutionary information and communication technologies, such as the internet, cloud computing, artificial intelligence, big data, and the Internet of Things (IoT). The Digital Revolution has changed almost every aspect of human life, including the way we work, communicate, shop, get information and seek entertainment.
Here are some key moments in the history of the Digital Revolution:
1960s: Development of the Internet At first, the internet was developed as a military research project called the ARPANET by the United States Department of Defense. In 1969, the ARPANET succeeded in sending its first message between two computers in two different locations. This is the beginning of the development of computer networks which later became the basis of the internet that we know today.
1970s: Early Computing In this decade, computers began to be widely adopted in the world of business and industry. This technology is used to automate tasks that were previously performed manually, increasing efficiency and productivity.
1980s: Personal Computers (PCs) The invention of the personal computer or personal computer (PC) brought a new revolution in technology. PCs made computer technology more accessible to the general public, changing the way we interact with technology.
The 1990s: The Internet's Golden Age In 1991, the World Wide Web (WWW) was created by Tim Berners-Lee, linking documents and resources on the internet via hypertext. This was an important milestone in the development of the internet which brought about an explosion of information and global connectivity.
Early 21st Century: The Age of Digitalization In the 21st century, there is an acceleration in digitization. Mobile devices such as smartphones and tablets are growing in popularity, giving millions of people worldwide access to the internet. Online services such as e-commerce, social media, and cloud-based applications are growing rapidly.
The 2010s: Artificial Intelligence and the Internet of Things (IoT) Artificial Intelligence (AI) and Internet of Things (IoT) are starting to dominate the world of technology. Artificial intelligence is used in a variety of applications, from facial recognition to product recommendations. IoT connects devices and objects around the world, creating a complex interconnected ecosystem.
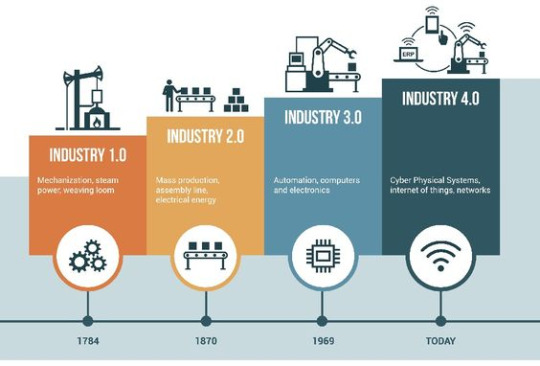
The Digital Revolution continues with the rapid development of technologies such as artificial intelligence, autonomous vehicles and biomedical technologies. In facing this change, it is important for us to continue to develop digital literacy, maintain data privacy and security, and optimize the benefits of digital technology to create a positive impact on society and our lives. The history of the Digital Revolution is a story of limitless innovation, progress and transformation.
13 notes
·
View notes
Text
Overcoming Challenges in Data Integration: Insights from Consulting Experts
Data integration for enterprises can take longer due to technological, financial, and time constraints. As a result, modifying data strategies to mitigate risks like incompatibility between many tools or budget overruns is crucial. Companies must also prepare for new compliance requirements to ensure ethical data operations. This post will explore such challenges in data integration while listing valuable insights from consulting experts in this domain.
What is Data Integration?
Data integration merges data from disparate origins and presents it to maximize comprehension, consolidation, and summarization effectiveness. Integrated data views rely on data ingestion, preparation, and advanced insight extraction. It also streamlines the data operations services across regulatory report creation, helpdesks, and 360-degree client life cycle management.
All data integration strategies involve the extract, transform, and load (ETL) pipelines regardless of business units or target industries. At the same time, the scope of planning and quality assurance in each process varies due to domain-specific data classification factors.
For instance, the accounting departments must handle extensive numerical data while interpreting legal and organizational requirements for transparency. On the other hand, production engineering and design professionals will use visualizations to improve goods or service packages. Accordingly, accountants will use unique tools distinct from engineers’ software.
Later, the leaders might want a comprehensive overview of the synergy between these departments. Therefore, they must determine efficient data integration strategies. The data will move between several programs, carrying forward many updates throughout a project’s progression based on those roadmaps.
Overcoming the Challenges in Data Integration Using Insights from Consulting Experts
1| Data Quality Hurdles
Linking, consolidating, and updating data from several sources will exponentially increase the quality-related threats. For instance, consider multimedia assets from social networks or unreliable news outlets. They can help your secondary market research and social listening initiatives. However, you want to verify the authenticity of gathered intelligence to avoid inaccurate data ingestion.
Evaluating relevance, freshness, and consistency is essential to data quality assurance from creation to archival. So, corporations have started leveraging data lifecycle management to boost dataset integrity, helping make integration less of a hassle.
Insights:
Most consulting experts suggest developing ecosystems that check and recheck quality metrics at each stage of a data integration lifecycle. Moreover, they recommend maintaining periodic data backups with robust version control mechanisms. Doing so will help quality preservation efforts if errors arise after a feature update or a malicious third party is likely to break the system using malware.
2| Networking and Computing Infrastructure Problems
Legacy hardware and software often introduce bottlenecks, hurting data integration’s efficiency. Modern integration strategies demand more capable IT infrastructure due to the breakthroughs like the internet of things (IoT), 5G networks, big data, and large language models. If a company fails to procure the necessary resources, it must postpone data integration.
Technologies integral to capturing, storing, checking, sorting, transferring, and encrypting data imply significant electricity consumption. Besides, a stable networking environment with adequate governance implementations enables secure data transactions. The underlying computing infrastructure is not immune to physical damage or downtime risks due to maintenance mishaps.
What Consulting Experts Say:
Enterprises must invest in reliable, scalable, and efficient hardware-software infrastructure. This will benefit them by providing a stable working environment and allowing employees to witness productivity improvements. Upgrading IT systems will also enhance cybersecurity, lowering the risk of zero-day vulnerabilities.
3| Data Availability Delays
Governments, global firms, educational institutions, hospitals, and import-export organizations have a vast network of regional offices. These offices must also interact with suppliers, contractors, and customers. Due to the scale of stakeholder engagement, reports concerning office-level performance and inventory might arrive late.
Underproductive employees, tech troubleshooting, slow internet connectivity, and a poor data compression ratio will make data sourcing, updating, and analyzing inefficient. As a result, a data integration officer must address time-consuming activities through strategic resource allocation. If left unaddressed, delays in data delivery will adversely affect conflict resolution and customer service.
Expert Insights:
Train your employees to maximize their potential and reduce data acquisition, categorization, and transformation delays. Additionally, you will want to embrace automation through artificial intelligence (AI) applications. Find methods to increase the data compression ratio and accelerate encryption-decryption processing cycles. These measures will help accomplish near-real-time data integration objectives.
4| Vendor Lock-ins
A vendor lock-in results from inconvenience and restrictions when a client wants to switch to another service provider or toolkit. Although data integration platforms claim they celebrate the ease of migrating databases with competitors, they might covertly create vendor lock-ins.
For instance, some data sourcing and sorting ecosystems might limit the supported formats for bulk export commands. Others will use misleading methods to design the graphical user interface (GUI) of account deletion and data export features. They involve too many alerts or generate corrupt export files.
Practical Insights:
Combining multiple proprietary and open-source software tools offers the best cost optimization opportunities. When you select a data vendor, audit the tools the willing data integration providers use to deliver their assistance. Do they use a completely proprietary system based on an unknown file format unsupported by other platforms?
Finally, you must check all the data import, export, and bulk transfer options in vendors’ documentation. After you check a data firm’s current client base, track its online ratings and scan for red flags indicating potential vendor lock-ins.
5| Data-Related Ethical and Legal Liabilities
Confidentiality of investor communication and stakeholders’ privacy rights are two components of legal risk exposure due to enterprise data integration. Additionally, brands must interpret industry guidelines and regional directives for regulatory disclosures.
They must comply with laws concerning personally identifiable information (PII) about employees and customers. Otherwise, they will attract policymakers’ ire, and customers will lose faith in brands that do not comply with the laws of their countries.
Insights:
Consulting experts recommend collaborating with regional legal teams and global governance compliance specialists. After all, mitigating legal risks can help increase business resilience.
Improved compliance ratings have also benefited several brands wanting to be attractive to impact investors. Meanwhile, customers demanding ethical data operations at business establishments love supporting brands with an exceptional governance culture.
Conclusion
Most brands need specialists' help to develop consolidated data views during reporting because they have flawed data integration strategies. So, they require trustworthy insights from reputed consulting experts with a proven track record of overcoming challenges in data integration. The selected data partners must excel at ETL implementation, governance compliance, and data quality management (DQM).
The corporate world champions data-centric business development. Understandably, the need for scalable data integration reflects the increased stakeholder awareness regarding the importance of connecting disparate data sources. With transparent, fast, and accurate data, organizations will enhance their competitive edge amid this intense digital transformation race.
3 notes
·
View notes
Text
Transforming the Health Landscape: The Global Blockchain in Healthcare Market

The integration of blockchain technology into the healthcare sector is revolutionizing the way medical data is managed, shared, and secured. As the demand for transparent, efficient, and secure healthcare services grows, blockchain offers promising solutions to longstanding challenges.
Understanding Blockchain in Healthcare
Blockchain Technology is a decentralized digital ledger that records transactions across multiple computers in a way that ensures the security and transparency of data. In healthcare, blockchain can be used to manage patient records, track pharmaceuticals, ensure the integrity of clinical trials, and streamline administrative processes. The immutable nature of blockchain helps in preventing data breaches, ensuring data accuracy, and enhancing patient privacy.
According to BIS Research, the Global Blockchain in Healthcare Market was estimated to grow to a value of $5.61 billion by 2025, and still the market is showing a steep growth till 2030 witnessing a double-digit CAGR growth rate throughout the forecast period.
Key Market Dynamics
Several factors are driving the growth of the global blockchain in healthcare market:
Data Security and Privacy:
Need for robust data security and privacy solutions.
Healthcare data breaches are a growing concern.
Blockchain's secure, immutable nature protects sensitive patient information.
Interoperability and Data Sharing:
Facilitates seamless data sharing between healthcare providers and systems.
Overcomes current interoperability issues.
Leads to better patient outcomes by providing a comprehensive view of health history.
Supply Chain Transparency:
Tracks the entire lifecycle of drugs in the pharmaceutical industry.
Ensures the authenticity of medications.
Helps combat counterfeit drugs.
Efficient Administrative Processes:
Streamlines various administrative processes, such as billing and claims management.
Reduces fraud and administrative costs.
Support from Regulatory Bodies:
Increasing support from regulatory bodies and governments.
Initiatives by FDA and EMA to explore blockchain for drug traceability and clinical trials boost market growth.
Request for an updated Research Report on Global Blockchain in Healthcare Market Research.
Global Blockchain in Healthcare Industry Segmentation
Segmentation by Application:
Data Exchange and Interoperability
Supply Chain Management
Claims Adjudication and Billing Management
Clinical Trials and Research
Others
Segmentation by End-User:
Healthcare Providers
Pharmaceutical Companies
Payers
Others
Segmentation by Region:
North America
Europe
Asia-Pacific
Latin America and Middle East & Africa
Future Market Prospects
The future of the global blockchain in healthcare market looks promising, with several trends likely to shape its trajectory:
Integration with AI and IoT: The integration of blockchain with artificial intelligence (AI) and the Internet of Things (IoT) will enhance data analytics, predictive healthcare, and real-time monitoring.
Expansion of Use Cases: New use cases for blockchain in digital healthcare will emerge, including patient-centered care models, personalized medicine, and enhanced telemedicine services.
Focus on Patient-Centric Solutions: Blockchain will enable more patient-centric healthcare solutions, empowering patients with greater control over their health data and enhancing patient engagement.
Development of Regulatory Frameworks: The establishment of clear regulatory frameworks and industry standards will facilitate the widespread adoption of blockchain in healthcare.
Conclusion
The Global Blockchain in Healthcare Industry is poised for significant growth, driven by the need for enhanced data security, interoperability, supply chain transparency, and efficient administrative processes. By addressing challenges related to regulatory compliance, implementation costs, standardization, and scalability, and leveraging opportunities in technological advancements, investments, partnerships, and government initiatives, the potential of blockchain in healthcare can be fully realized. This technology promises to revolutionize healthcare delivery, enhancing efficiency, transparency, and patient outcomes, and setting new standards for the future of digital health.
#Blockchain in Healthcare Market#Blockchain in Healthcare Industry#Blockchain in Healthcare Market Report#Blockchain in Healthcare Market Research#Blockchain in Healthcare Market Forecast#Blockchain in Healthcare Market Analysis#Blockchain in Healthcare Market Growth#BIS Research#Healthcare
2 notes
·
View notes
Text
Java's Lasting Impact: A Deep Dive into Its Wide Range of Applications
Java programming stands as a towering pillar in the world of software development, known for its versatility, robustness, and extensive range of applications. Since its inception, Java has played a pivotal role in shaping the technology landscape. In this comprehensive guide, we will delve into the multifaceted world of Java programming, examining its wide-ranging applications, discussing its significance, and highlighting how ACTE Technologies can be your guiding light in mastering this dynamic language.

The Versatility of Java Programming:
Java programming is synonymous with adaptability. It's a language that transcends boundaries and finds applications across diverse domains. Here are some of the key areas where Java's versatility shines:
1. Web Development: Java has long been a favorite choice for web developers. Robust and scalable, it powers dynamic web applications, allowing developers to create interactive and feature-rich websites. Java-based web frameworks like Spring and JavaServer Faces (JSF) simplify the development of complex web applications.
2. Mobile App Development: The most widely used mobile operating system in the world, Android, mainly relies on Java for app development. Java's "write once, run anywhere" capability makes it an ideal choice for creating Android applications that run seamlessly on a wide range of devices.
3. Desktop Applications: Java's Swing and JavaFX libraries enable developers to craft cross-platform desktop applications with sophisticated graphical user interfaces (GUIs). This cross-platform compatibility ensures that your applications work on Windows, macOS, and Linux.
4. Enterprise Software: Java's strengths in scalability, security, and performance make it a preferred choice for developing enterprise-level applications. Customer Relationship Management (CRM) systems, Enterprise Resource Planning (ERP) software, and supply chain management solutions often rely on Java to deliver reliability and efficiency.
5. Game Development: Java isn't limited to business applications; it's also a contender in the world of gaming. Game developers use Java, along with libraries like LibGDX, to create both 2D and 3D games. The language's versatility allows game developers to target various platforms.
6. Big Data and Analytics: Java plays a significant role in the big data ecosystem. Popular frameworks like Apache Hadoop and Apache Spark utilize Java for processing and analyzing massive datasets. Its performance capabilities make it a natural fit for data-intensive tasks.
7. Internet of Things (IoT): Java's ability to run on embedded devices positions it well for IoT development. It is used to build applications for smart homes, wearable devices, and industrial automation systems, connecting the physical world to the digital realm.
8. Scientific and Research Applications: In scientific computing and research projects, Java's performance and libraries for data analysis make it a valuable tool. Researchers leverage Java to process and analyze data, simulate complex systems, and conduct experiments.
9. Cloud Computing: Java is a popular choice for building cloud-native applications and microservices. It is compatible with cloud platforms such as AWS, Azure, and Google Cloud, making it integral to cloud computing's growth.

Why Java Programming Matters:
Java programming's enduring significance in the tech industry can be attributed to several compelling reasons:
Platform Independence: Java's "write once, run anywhere" philosophy allows code to be executed on different platforms without modification. This portability enhances its versatility and cost-effectiveness.
Strong Ecosystem: Java boasts a rich ecosystem of libraries, frameworks, and tools that expedite development and provide solutions to a wide range of challenges. Developers can leverage these resources to streamline their projects.
Security: Java places a strong emphasis on security. Features like sandboxing and automatic memory management enhance the language's security profile, making it a reliable choice for building secure applications.
Community Support: Java enjoys the support of a vibrant and dedicated community of developers. This community actively contributes to its growth, ensuring that Java remains relevant, up-to-date, and in line with industry trends.
Job Opportunities: Proficiency in Java programming opens doors to a myriad of job opportunities in software development. It's a skill that is in high demand, making it a valuable asset in the tech job market.
Java programming is a dynamic and versatile language that finds applications in web and mobile development, enterprise software, IoT, big data, cloud computing, and much more. Its enduring relevance and the multitude of opportunities it offers in the tech industry make it a valuable asset in a developer's toolkit.
As you embark on your journey to master Java programming, consider ACTE Technologies as your trusted partner. Their comprehensive training programs, expert guidance, and hands-on experiences will equip you with the skills and knowledge needed to excel in the world of Java development.
Unlock the full potential of Java programming and propel your career to new heights with ACTE Technologies. Whether you're a novice or an experienced developer, there's always more to discover in the world of Java. Start your training journey today and be at the forefront of innovation and technology with Java programming.
8 notes
·
View notes
Text
Raspberry Pi Board: Revolutionizing Computing and Education

The Raspberry Pi board is a series of small, affordable single-board computers developed by the Raspberry Pi Foundation, a UK-based charity focused on promoting computer science education and digital literacy. Since its launch in 2012, the Raspberry Pi has transformed from a niche educational tool into a versatile platform used in a wide range of applications, from DIY electronics projects to industrial automation.
A Brief History
The first Raspberry Pi, the Model B, was released in February 2012. Designed to promote basic computer science in schools and developing countries, it featured a 700 MHz ARM11 processor, 256 MB of RAM, and basic connectivity options. The success of the Model B led to a rapid expansion of the Raspberry Pi lineup, with various models offering improved performance, more memory, and enhanced connectivity.
Key Features and Models
Raspberry Pi 1 Model B (2012):
Processor: 700 MHz ARM11
Memory: 256 MB RAM
Ports: 2 USB 2.0 ports, HDMI, Composite video, 3.5mm audio jack, Ethernet
Storage: SD card slot
Raspberry Pi 2 Model B (2015):
Processor: 900 MHz quad-core ARM Cortex-A7
Memory: 1 GB RAM
Ports: 4 USB 2.0 ports, HDMI, Composite video, 3.5mm audio jack, Ethernet
Storage: MicroSD card slot
Raspberry Pi 3 Model B (2016):
Processor: 1.2 GHz quad-core ARM Cortex-A53
Memory: 1 GB RAM
Ports: 4 USB 2.0 ports, HDMI, Composite video, 3.5mm audio jack, Ethernet
Wireless: Wi-Fi and Bluetooth
Raspberry Pi 4 Model B (2019):
Processor: 1.5 GHz quad-core ARM Cortex-A72
Memory: Options of 2 GB, 4 GB, and 8 GB RAM
Ports: 2 USB 3.0 ports, 2 USB 2.0 ports, 2 Micro HDMI ports, Ethernet, USB-C for power
Wireless: Wi-Fi and Bluetooth
Raspberry Pi Zero (2015) and Zero W (2017):
Processor: 1 GHz single-core ARM11
Memory: 512 MB RAM
Ports: Mini HDMI, Micro USB OTG, Micro USB for power, GPIO pins
Wireless (Zero W): Wi-Fi and Bluetooth
Applications and Uses
The versatility of the Raspberry Pi has led to its adoption in numerous fields:
Education:
Coding and Programming: Used in schools and educational programs to teach students programming languages such as Python, Scratch, and Java.
Computer Science Concepts: Introduces concepts like hardware, software, and networking.
DIY Projects and Maker Community:
Home Automation: Controls smart home devices, including lights, thermostats, and security systems.
Media Centers: Powers home media centers using software like Kodi.
Retro Gaming: Emulates classic gaming consoles using software like RetroPie.
Industrial and Commercial Applications:
IoT Devices: Serves as a hub for Internet of Things (IoT) devices, enabling data collection and remote control.
Automation and Control Systems: Used in factories and labs for monitoring and controlling equipment.
Research and Development:
Prototyping: Facilitates rapid prototyping of electronic devices and systems.
Data Collection: Gathers data from various sensors in environmental and scientific research.
Community and Ecosystem
The Raspberry Pi has cultivated a vibrant global community of developers, hobbyists, educators, and students. Online forums, tutorials, and community projects provide extensive support and resources for users at all skill levels. The Raspberry Pi Foundation also offers official accessories, including cases, cameras, and expansion boards, further enhancing the functionality of the Raspberry Pi.
Conclusion
The Raspberry Pi board has revolutionized the way people learn about and interact with technology. Its affordability, versatility, and extensive support network have made it an indispensable tool in education, DIY projects, and professional applications. As technology continues to evolve, the Raspberry Pi Foundation remains committed to expanding the capabilities and accessibility of this remarkable platform, ensuring that computing remains within reach for everyone.
3 notes
·
View notes